Recently, Microsoft announced a significant global tech outage affecting approximately 8.5 million Windows devices. The source of this disruption was a software update by the cybersecurity firm CrowdStrike, which caused widespread issues across various industries. Users around the world were unable to log into their systems as their devices crashed after being switched on. Social media users even coined the term ‘Happy International Blue Screen Day’ in light of the widespread Blue Screen of Death (BSOD) errors.
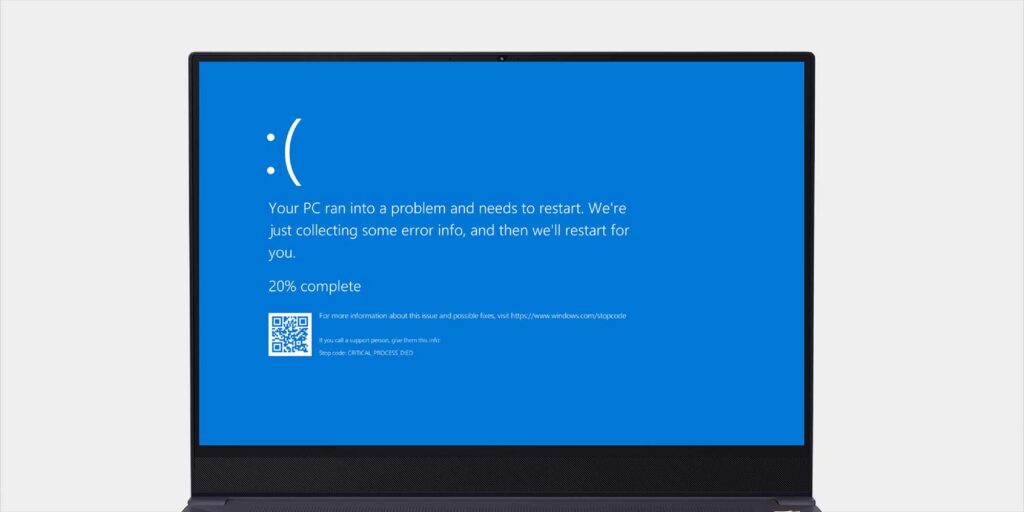
The Scope of the Outage
Windows outage issues have led to users being logged out of their systems and stuck in recovery mode. The problem originated from a recent update by CrowdStrike, a US-based cybersecurity company that provides endpoint security to several organizations globally. Microsoft revealed that less than one percent of all Windows machines were affected, but this still amounted to millions of devices worldwide.

Collaborative Efforts for Resolution
To address the situation, CrowdStrike partnered with Microsoft to develop a scalable solution aimed at resolving the issue swiftly. Microsoft also engaged with other tech giants, such as Amazon Web Services (AWS) and Google Cloud Platform, to determine the most effective ways to fix the problem. This collaborative effort focused on restoring normal operations and minimizing further disruptions. While the scale of the outage was significant, the combined efforts of Microsoft and its partners are working to ensure a quick recovery.
Response from Threatsys
At Threatsys, the leading cybersecurity company of India, we notified all of our clients across the world about the issue and helped them fix it according to the notification by CrowdStrike and CERT-In. Our CEO, Mr. Deepak Kumar Nath, briefed media outlets about the issues and solutions from the first day. He discussed the issue, how it can be resolved, and how similar incidents can be prevented in the future.

BSOD Error in Latest CrowdStrike Update:
Many Windows machines experienced blue screens or were stuck in recovery mode.
Symptoms include:
• Hosts experiencing a bug check/blue screen error related to the Falcon Sensor.
• Windows hosts not impacted do not require any action as the problematic channel file has been reverted.
• Windows hosts brought online after 0527 UTC will also not be impacted.
• This issue does not affect Mac- or Linux-based hosts.
• The channel file “C-00000291.sys” with a timestamp of 0527 UTC or later is the reverted (good) version. • The channel file “C-00000291.sys” with a timestamp of 0409 UTC is the problematic version.
Possible Workaround Steps:
• Boot Windows into Safe Mode or the Windows Recovery Environment.
• Navigate to the C:\Windows\System32\drivers\CrowdStrike directory.
• Locate and delete the file matching “C-00000291.sys”.
• Boot the host normally.
For Public Cloud or Virtual Environments:
Option 1:
• Detach the operating system disk volume from the impacted virtual server. • Create a snapshot or backup of the disk volume as a precaution. • Attach/mount the volume to a new virtual server. • Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory. • Locate and delete the file matching “C-00000291.sys”.
• Detach the volume from the new virtual server.
• Reattach the fixed volume to the impacted virtual server.
Option 2:
• Roll back to a snapshot before 0409 UTC.
Workaround Steps for Azure via Serial:
• Log in to the Azure console –> Go to Virtual Machines –> Select the VM.
• Click “Connect” –> “More ways to Connect” –> “Serial Console”.
• Once SAC has loaded, type ‘cmd’ and press enter.
• Enter Administrator credentials.
• Type the following:
• bcdedit /set {current} safeboot minimal
• bcdedit /set {current} safeboot network
• Restart the VM.
Shared Notification of CERT-In to All Clients of Threatsys
CrowdStrike, a prominent XDR (Extended Detection and Response) provider, encountered a significant technical issue that affected numerous organizations. On July 18, 2024, a Blue Screen of Death (BSOD) issue associated with CrowdStrike’s Falcon sensor update caused widespread disruptions. The BSOD is a critical system error in Windows that forces a restart, often leading to data loss and operational downtime. This error impacted hundreds of thousands of devices globally, affecting sectors such as healthcare, banking, transportation, and government services.
The CYQER Approach: Avoiding Similar Risks
Unlike CrowdStrike, CYQER, Threatsys’s flagship all-in-one SOC platform, adopts a different approach. As a worldwide leader in cybersecurity, we are dedicated to constantly innovating to facilitate secure digital transformation, even in the face of rapidly accelerating change.
CYQER: Cyber Yield Quantification for Enterprises and Reporting – All Capabilities in One
Our CYQER platform provides Security Operations Center (SOC) services to help organizations build their strongest defense against cybercrime and maximize return on investment. With CYQER, you can rest easy knowing that you have a team of experts monitoring your systems and ensuring that your organization is protected from cyber threats. Our product received the latest updates and helped our clients use it.
Key Aspects of CYQER’s Approach:
• User Space Operations: CYQER agents run in the user space rather than the kernel space, avoiding direct access to the core operating system and mitigating the risk of critical system errors.
• Standard Kernel APIs: CYQER interacts with the operating system using standard kernel APIs, ensuring compatibility and stability without the complexities of high-risk kernel drivers.
Advantages of User Space Operations:
• Enhanced Stability: User space applications are less likely to cause system-wide crashes, providing a more stable environment.
• Easier Debugging: Issues in the user space are easier to diagnose and fix compared to those in the kernel space.
• Improved Security: Limiting access to the core operating system reduces the attack surface for potential exploits.
Conclusion
The recent CrowdStrike BSOD incident highlights the risks associated with kernel drivers in security software. CYQER’s emphasis on user space operations and standard kernel APIs provides a safer and more reliable alternative. This approach ensures security monitoring and threat protection without compromising system stability. At Threatsys, we remain committed to helping our clients navigate and resolve such issues promptly, ensuring minimal disruption to their operations.

Increase your preparedness,
Solidify your security stance





