When most people think of the internet, they imagine Google searches, social media, and online shopping. But this visible web is just the tip of the iceberg. Beneath it lies the deep web and dark web hidden layers where cybercriminals trade stolen credentials, leak ransomware data, and sell zero-day exploits.
The big question is: How can organizations defend against threats they can’t even see?
That’s where Threatsys Intelligence Wing, a dark web monitoring and intelligence platform, steps in. Unlike traditional security tools, Threatsys Intelligence Wing dives into hidden corners of the internet, uncovering the risks that quietly shape tomorrow’s cyberattacks.
The Dark Web: A Criminal Playground
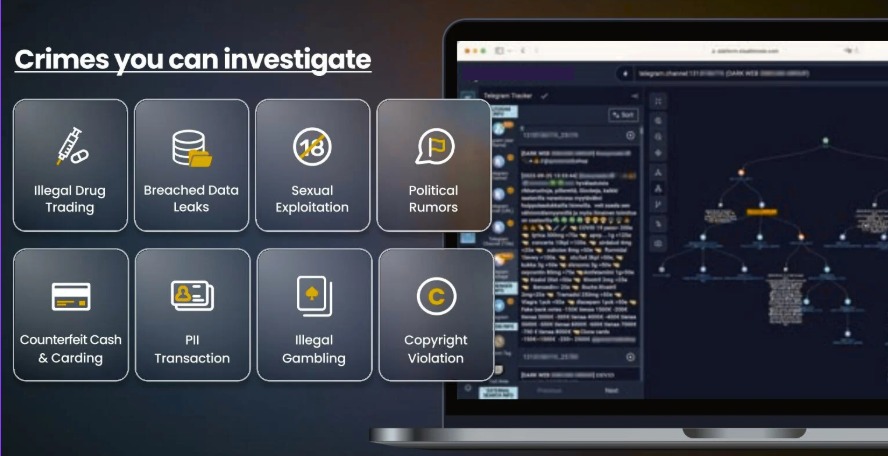
Credential dumps, ransomware extortion, illegal marketplaces, and malware kits are exchanged daily in underground forums. These spaces are invisible to search engines but serve as breeding grounds for attackers.
Threatsys Intelligence Wing continuously scans these hidden networks, ensuring organizations stay aware of critical risks that could otherwise remain unseen.
Compromised Credentials: The New Skeleton Key
Passwords leaked in one breach often unlock dozens of accounts elsewhere. Cybercriminals exploit this password reuse to move quickly between systems.
Compromised Credential Monitoring from Threatsys Intelligence Wing detects exposures early, allowing security teams to reset, block, or investigate before attackers gain access.
Ransomware Leaks on the Dark Web
Ransomware has evolved into a double extortion model: if victims refuse to pay, gangs publish stolen data on dark web leak sites.
Threatsys Intelligence Wing’s Ransomware Monitoring keeps watch over these portals. If your organization’s name or data appears, you’re alerted instantly, so incident response begins immediately, not months later.
Telegram & Hidden Networks Monitoring
Encrypted messaging platforms like Telegram have become popular among cybercriminals for selling phishing kits, stolen databases, and malware.
With its Telegram Tracker and Darkweb Map, Threatsys Intelligence Wing uncovers hidden conversations, tracks criminal groups, and visualizes how underground networks connect—making the invisible visible.
From Data to Actionable Threat Intelligence
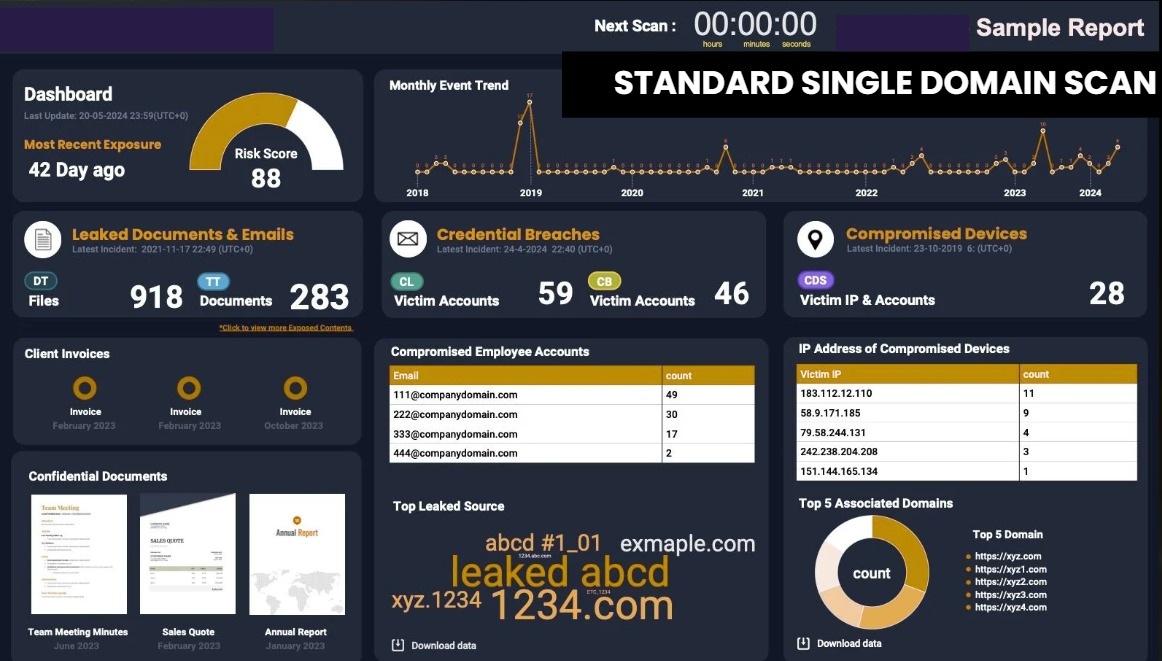
Raw data alone isn’t enough. Threatsys Intelligence Wing transforms scattered information into clear, actionable insights through:
- Data Acquisition → Parsing & Indexing – cleaning hidden-source data.
- 52 Threat Indicators – IPs, domains, wallets, emails, hashes, credentials.
- Investigation Canvas – connecting leaks, wallets, IPs, and usernames into a single investigative flow.
- APIs & Integrations – delivering intelligence into SIEM, EDR, and SOAR systems.
How Threatsys Intelligence Wing Keeps You Ahead of Dark Web Threat

- Compromised Credential Alerts
Leaked passwords are often reused across multiple accounts, giving attackers easy access. Threatsys Intelligence Wing monitors underground forums and breach dumps to instantly alert you if employee or customer credentials surface, so you can reset, block, or investigate before damage occurs. - Ransomware Leak Detection
Ransomware gangs now publish stolen data on leak sites if victims refuse to pay. Threatsys Intelligence Wing continuously tracks these portals and notifies you the moment your organization’s name or data appears, enabling faster incident response and limiting reputational fallout. - Telegram & Dark Web Monitoring
Cybercriminals operate in encrypted channels like Telegram and hidden forums to share phishing kits, malware, and stolen data. Threatsys Intelligence Wing infiltrates and maps these networks, giving visibility into underground groups and their activities. - Investigation Canvas
Threat data is often scattered a leaked email here, a wallet address there. Threatsys Intelligence Wing’s Investigation Canvas connects these pieces into a single investigative flow, helping analysts uncover relationships and trace threats back to their source. - API & SIEM Integration
Intelligence is only valuable if it’s actionable. With API and SIEM integration, Threatsys Intelligence Wing feeds real-time insights directly into your SOC tools (SIEM, EDR, SOAR), ensuring security teams can respond without delay.
Conclusion: You Can’t Defend What You Can’t See
The deep and dark web aren’t myths ,they’re thriving ecosystems that fuel ransomware, fraud, and identity theft every day.
With Threatsys Intelligence Wing, organizations gain visibility into these hidden layers of the internet. By combining AI-powered monitoring with investigative tools, the platform ensures you stay ahead of tomorrow’s attacks by detecting what others overlook.
At Threatsys, we don’t just secure your systems — we future-proof your growth.

Stay secure, stay resilient with Threatsys.





