Cyberattacks today are more targeted, persistent, and damaging than ever before. Firewalls and antivirus tools alone are no longer enough to protect modern organizations. What truly matters is how well an organization can think like an attacker, defend like a strategist, and continuously improve. This is where Red Team, Blue Team, and Purple Team approaches become critical.
At Threatsys, we follow a practical, real-world security mindset—one that blends offensive testing, defensive readiness, and continuous collaboration. This optimized guide explains Red, Blue, and Purple Teams in a clear, business-relevant way, without unnecessary complexity.
Understanding the Red Team
A Red Team simulates real-world cyberattacks to uncover weaknesses before adversaries exploit them. Instead of surface-level testing, Red Team exercises mirror the mindset, tools, and persistence of real attackers.
Their objective is simple but powerful: test how far an attacker can go without being detected.
Core focus areas of a Red Team include:
- Gaining unauthorized access to systems and networks
- Exploiting misconfigurations, unpatched assets, and weak credentials
- Bypassing security controls and monitoring mechanisms
- Testing human vulnerabilities through social engineering
Red Teaming answers a critical business question: “If an actual attacker targets us today, what would they realistically achieve?”
Understanding the Blue Team
The Blue Team represents the defensive side of cybersecurity. Their role is to continuously protect systems, detect suspicious activity, and respond to incidents before they escalate into business-impacting breaches.
While Red Teams test security assumptions, Blue Teams ensure operational resilience.
Key responsibilities of a Blue Team include:
- Continuous monitoring of networks, endpoints, and logs
- Threat detection, investigation, and incident response
- Vulnerability management and patch governance
- Improving visibility and response readiness across the environment
A strong Blue Team minimizes downtime, limits damage, and keeps the organization operational during attacks.
Understanding the Purple Team
A Purple Team is not a standalone unit—it is a collaborative approach that connects Red and Blue Teams to maximize security outcomes.
Instead of working in silos, Purple Teaming ensures attack techniques and defensive gaps are openly shared, analyzed, and improved.
Purple Teaming typically focuses on:
- Mapping Red Team attack techniques to Blue Team detection capabilities
- Identifying blind spots in monitoring and response
- Fine-tuning security controls and playbooks
- Creating a continuous feedback and improvement loop
This approach shifts cybersecurity from periodic testing to continuous security maturity.
Red vs Blue vs Purple Team – Key Differences
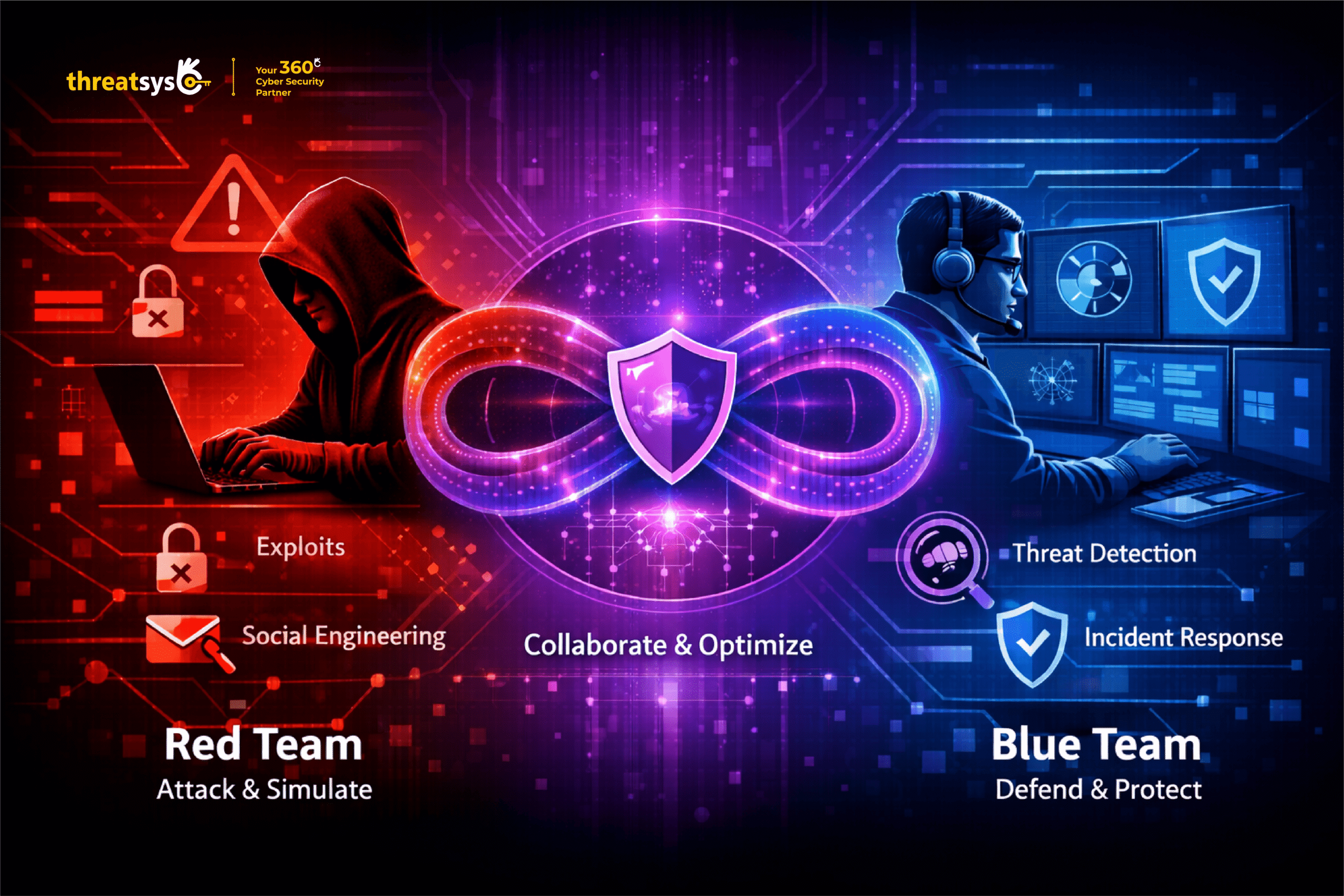
Each team plays a distinct role in strengthening cybersecurity posture:
- Red Team focuses on offensive security and attack simulation
- Blue Team focuses on defense, monitoring, and incident response
- Purple Team focuses on collaboration, optimization, and improvement
Together, they create a balanced and realistic security strategy that reduces blind spots and strengthens resilience.
Least Privilege Access
Access is granted only to what is strictly required for a specific task and for a limited duration. By eliminating unnecessary permissions, Zero Trust:
- Reduces the blast radius of compromised accounts
- Prevents privilege escalation
- Limits the impact of insider threats
Even if an attacker gains access, their ability to move or cause damage is heavily restricted.
Why Modern Organizations Need All Three
Relying only on defensive tools can create a false sense of security. Similarly, running isolated penetration tests without improving defenses limits long-term value. The strongest security programs combine all three approaches.
At Threatsys, we have observed that organizations adopting Purple Team methodologies reduce detection time, improve incident response maturity, and strengthen their overall cyber resilience.
This integrated approach is especially critical for industries such as finance, healthcare, government, critical infrastructure, and large enterprises where downtime and data loss carry serious consequences.
How Threatsys Can Help
![]()
Threatsys provides end-to-end cybersecurity services designed around real-world attack scenarios and measurable defense outcomes.
Our Red Team services help organizations:
- Simulate advanced and targeted attack scenarios
- Identify hidden vulnerabilities beyond standard scans
- Test detection, response, and escalation mechanisms
Our Blue Team services focus on:
- Strengthening monitoring, detection, and incident response
- Improving SOC efficiency and response maturity
- Reducing dwell time and business impact during attacks
Our Purple Team engagements enable:
- Direct collaboration between offensive and defensive teams
- Faster closure of security gaps identified during attacks
- Continuous improvement of security controls and processes
This integrated approach ensures security is not just tested, but continuously strengthened
Conclusion
Cybersecurity is no longer a static defense problem—it is an ongoing process of testing, defending, and improving. Red Teams expose weaknesses, Blue Teams protect critical assets, and Purple Teams ensure both evolve together. Organizations that adopt this balanced model move beyond reactive security and build long-term cyber resilience against modern threats.
With Threatsys, cybersecurity becomes a continuous, intelligence-driven capability rather than a one-time exercise.

Stay secure, stay aware with Threatsys.





