Another Day, Another Cyberattack—This Time It’s CoinDCX
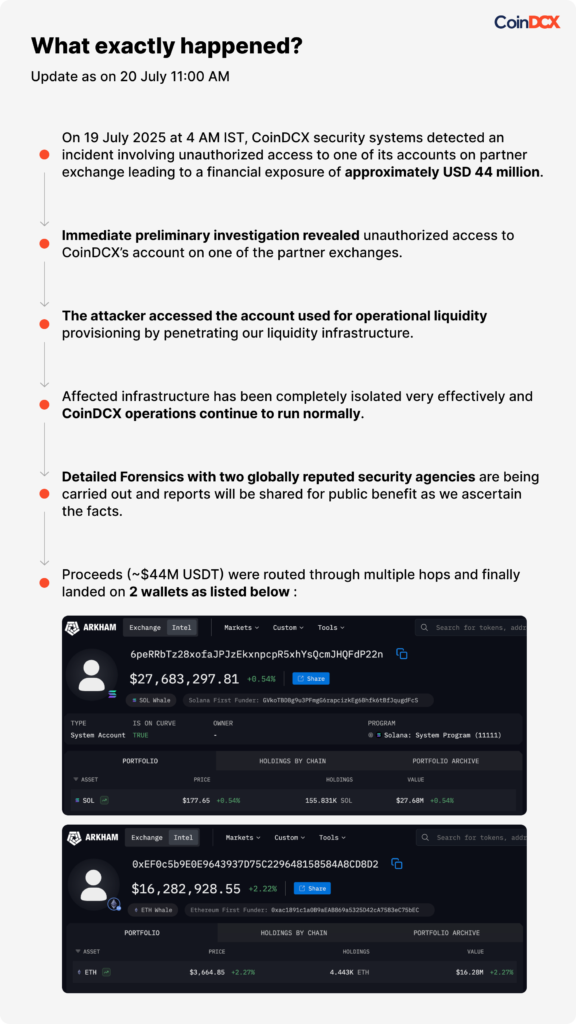
In a shocking blow to the Indian crypto ecosystem, CoinDCX—India’s largest cryptocurrency exchange—was hacked, resulting in a staggering loss of $44 million (₹368 crore). The breach, confirmed by CoinDCX on July 21, 2025, has once again exposed the glaring vulnerabilities in hot wallet infrastructure and the urgent need for multi-layered cybersecurity in crypto and Web3 environments.
At Threatsys, we go beyond reporting—we decode what happened and provide strategic, actionable solutions to prevent it from happening again.
What Happened in the CoinDCX Cyber Breach?
While CoinDCX has yet to reveal the full technical details of the breach, initial insights indicate:
- The attackers exploited vulnerabilities in the platform’s hot wallets—which are inherently more exposed due to constant internet connectivity.
- Funds were drained stealthily into unidentified wallets.
- Withdrawals have been paused, and the exchange claims user funds are “safe”—yet the damage to user trust and brand credibility is already done.
- Law enforcement and cyber forensic teams are actively investigating the incident.
The Real Cost of Weak Crypto Security
This wasn’t just a financial attack—it was a complete breakdown of cyber resilience.
Consequences of the breach include:
- Loss of user confidence
- Legal and compliance repercussions
- Operational disruption
- Reputational damage that could take years to recover
And it all stems from overlooking basic cyber hygiene and scalable threat defense.
How Threatsys Secures Crypto Platforms and Web3 Startups
With hackers targeting exchanges, wallets, and DeFi platforms daily, it’s no longer enough to “react” after the fact. At Threatsys, we help crypto companies build cyber-resilient, attack-proof ecosystems.
Our Crypto Cybersecurity Services Include:
Vulnerability Assessment & Penetration Testing (VAPT)
We simulate real-world hacker tactics to uncover vulnerabilities in:
- Hot & cold wallets
- Crypto trading platforms
- APIs, smart contracts, and mobile apps
Ensuring robust security in the crypto space starts with comprehensive VAPT for crypto platforms. Through specialized penetration testing for crypto systems, vulnerabilities in smart contracts, exchanges, and infrastructure can be identified before attackers exploit them. At Threatsys, we also offer advanced wallet security testing to protect hot and cold wallets from unauthorized access, exploits, and operational risks.
24/7 SOC Monitoring for Wallet Infrastructure
Our Security Operations Center (SOC) offers:
- Real-time threat detection
- Transaction monitoring
- Anomaly alerts before funds are drained
To combat evolving threats in the digital asset space, a Crypto SOC (Security Operations Center) is essential for real-time threat detection and response. Threatsys provides 24/7 wallet monitoring to track unusual behavior and secure digital assets. Our systems also enable transaction anomaly detection, helping identify suspicious activity before it turns into a full-blown breach.
Smart Contract & Web3 Audits
We audit your smart contracts to detect:
- Logic flaws
- Vulnerable coding patterns
- Backdoors & permission escalation issues
In the Web3 ecosystem, security is non-negotiable. A thorough Web3 audit is the first step to identifying and fixing hidden risks in decentralized platforms. Threatsys specializes in smart contract security audits to uncover logic flaws, reentrancy issues, and other exploitable bugs. We also conduct blockchain vulnerability assessments to ensure end-to-end protection across your entire decentralized infrastructure.
Incident Response & Forensics
Already hacked? We respond within hours:
- Breach containment
- Wallet tracing
- Digital forensics for law enforcement coordination
When a breach hits, speed and clarity are critical. Threatsys offers rapid crypto incident response services to contain threats, minimize damage, and restore trust. Our expert team also conducts in-depth forensic investigations of crypto hacks, tracing attacker footprints across wallets, smart contracts, and blockchain bridges to uncover how the breach occurred and who was behind it.
Zero Trust Architecture for Crypto Apps
We implement Zero Trust Security Models that enforce:
- Identity verification for every access request
- Role-based access control
- Insider threat mitigation
In the world of digital assets, trust is a vulnerability. Threatsys helps implement zero trust for crypto platforms, ensuring that every user, device, and request is verified—every time. With robust crypto access control frameworks, we minimize unauthorized exposure and enforce least-privilege policies. Our approach also strengthens internal threat security, protecting against risks that often originate from within the organization.
Cyber Awareness & Phishing Simulation
Your team is your first line of defense. We train your staff to:
- Identify phishing attempts
- Avoid credential leaks
- Maintain best security practices daily
Human error remains one of the biggest threats in crypto security. Threatsys offers tailored crypto awareness training to educate teams on evolving attack tactics, wallet hygiene, and social engineering threats. We also run phishing simulations for crypto teams to test real-world readiness and build a proactive security culture across your organization.
Why Crypto Security Isn’t Optional Anymore
The CoinDCX hack is not an isolated incident—it’s a reminder that even industry leaders can fall when cybersecurity takes a backseat. Whether you’re managing millions in assets or building the next DeFi app, proactive protection is no longer a luxury—it’s a necessity.
Don’t wait until you’re breached. Be resilient from Day One.
Conclusion: Defend Your Crypto Exchange Before It’s Too Late
At Threatsys, we’ve protected dozens of crypto exchanges, NFT platforms, and Web3 startups from multi-vector cyberattacks. We don’t just scan and audit—we simulate, stress-test, monitor, and fortify.Let’s evaluate your current security posture and identify the weak spots—before attackers do.

Have a Security Concern? We’re Just One Click Away.