A critical zero-day vulnerability in Microsoft SharePoint Server, tracked as CVE-2025-53770 (CVSS 9.8), is being actively exploited in a widespread campaign dubbed ToolShell. The flaw enables unauthenticated remote code execution (RCE) by leveraging deserialization of untrusted data in SharePoint’s _layouts/15/ToolPane.aspx endpoint.
Microsoft has since released security patches for both CVE-2025-53770 and a newly discovered related flaw CVE-2025-53771, which further hardens defenses around earlier vulnerabilities CVE-2025-49704 and CVE-2025-49706.
This campaign has already compromised over 85 SharePoint servers across 29 organizations, including multinational corporations and government entities.
About the Vulnerability: CVE-2025-53770
“Deserialization of untrusted data in on-premises SharePoint Server allows an unauthorized attacker to execute code remotely over a network.”
— Microsoft Security Advisory, July 19, 2025
Key Points:
- Impact: Remote Code Execution (RCE) without authentication
- Attack Vector: Network-based, via ToolPane.aspx
- Related Flaws: CVE-2025-49704 (RCE), CVE-2025-49706 (Spoofing), CVE-2025-53771 (New)
- Affected: SharePoint Server 2016, 2019, and Subscription Edition (on-prem only)
- Cloud SharePoint (Microsoft 365): NOT impacted
Understanding the ToolShell Exploit Chain
Threat actors are chaining the vulnerabilities in the following sequence:
- Spoofing via CVE-2025-49706
Exploits HTTP referer header handling to bypass authentication. - Remote Code Execution via CVE-2025-49704
Payload POSTed to ToolPane.aspx, deserializing malicious objects. - Bypass & Weaponization via CVE-2025-53770
Turns spoofing + deserialization into full RCE without prior auth. - MachineKey Theft & Persistence
Attackers use PowerShell to extract ValidationKey and DecryptionKey, enabling them to:- Forge valid __VIEWSTATE payloads
- Persist access even after reboots
- Bypass authentication in future sessions
- Lateral Movement & Obfuscation
Using valid-looking ViewState objects and stolen machine keys, attackers blend into legitimate SharePoint operations.
Technical Exploitation Steps
Step-by-Step Breakdown of How the Exploit Works:
Step 1: Target the Vulnerable Endpoint
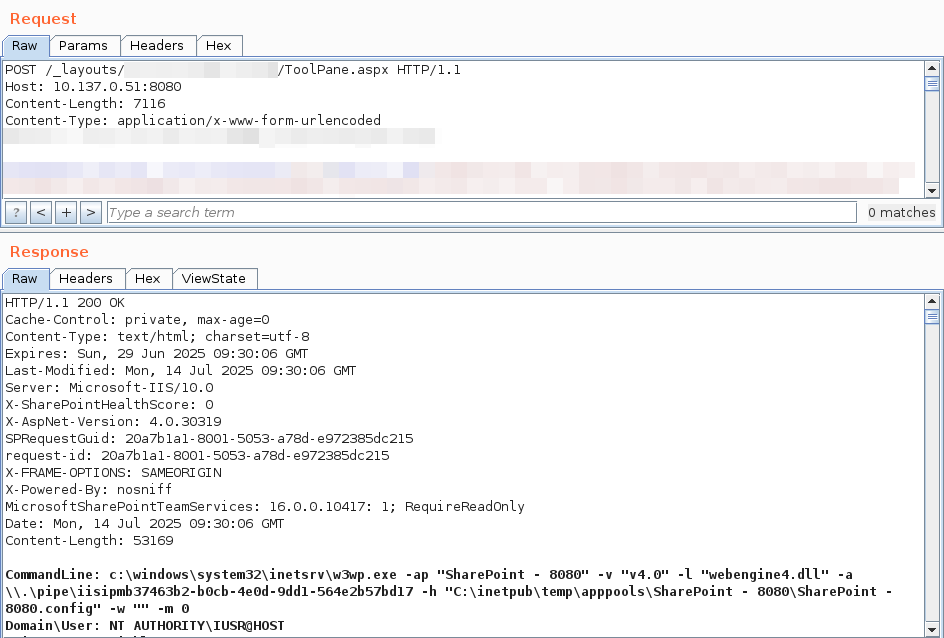
The attacker sends a crafted HTTP POST request to:
/_layouts/15/ToolPane.aspx?DisplayMode=Edit
This endpoint is typically used for managing web parts in SharePoint.
Step 2: Inject Malicious Payload
The POST body contains serialized data that abuses deserialization flaws in SharePoint’s view state mechanism. This may include embedded .NET objects or shellcode.
Step 3: Web Shell Deployment
A malicious ASPX web shell (e.g., shell.aspx) is saved to:
C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\
Step 4: Remote Code Execution via PowerShell
The shell runs PowerShell commands like:
powershell.exe -EncodedCommand <Base64Payload>
Used for:
- Creating new admin users
- Dumping credentials
- Lateral movement
Step 5: Persistence & Data Exfiltration
Attackers schedule tasks or registry entries and exfiltrate sensitive data over encrypted HTTP.
 What Makes This Campaign So Dangerous?
What Makes This Campaign So Dangerous?
- Unauthenticated Exploitation: No credentials are required to initiate the attack.
- Bypass of Prior Fixes: CVE-2025-53770 and 53771 bypass earlier July 2025 patches.
- __VIEWSTATE Forgery: Exploiting cryptographic signing mechanisms for stealthy persistence.
- Mass Exploitation Ongoing: Over 85 servers already infected with malicious ASPX web shells.
Microsoft’s Mitigation Guidance
In the absence of a patch (now released), Microsoft had urged the following:
- Enable AMSI integration (default in 23H2 and Sep 2023 updates)
- Deploy Microsoft Defender Antivirus
- Isolate unpatched servers by disconnecting from the internet
- Enable Defender for Endpoint for real-time telemetry and exploit detection
Important: Patch CVE-2025-53770 and CVE-2025-53771 immediately — these contain hardened fixes for previously bypassed exploits.
How Threatsys Is Responding to ToolShell
As part of our Cyber Emergency Response Framework (CERF), Threatsys has launched a Zero-Day Exploit Response Program for all affected organizations.
Our Immediate Action Plan
1. Rapid Vulnerability Assessment
- Scan all SharePoint instances
- Check patch levels and presence of vulnerable endpoints
2. Exploit Forensics & IOC Sweeps
- Detection of malicious ASPX shells
- Hunting for __VIEWSTATE manipulation and MachineKey access
3. Patch Management & Configuration Hardening
- Apply Microsoft’s CVE-2025-53770 and 53771 updates
- Rotate MachineKeys to prevent post-patch persistence
4. Behavioral Monitoring via Threatsys SOC
- Live 24×7 monitoring for post-exploit activities
- Threat intelligence feeds updated in real-time
5. Incident Response & Recovery
- Isolate compromised hosts
- Remove persistence mechanisms
- Restore secure configuration baselines
Strategic Recommendations from Threatsys
-
Patch Immediately: Apply the latest Microsoft security updates
-
Audit SharePoint Configs: Especially around MachineKey and access controls
-
Review Logs: Look for PowerShell usage, Referer spoofing, ViewState anomalies
-
Segment Access: Restrict internet access for internal collaboration systems
-
Engage a Security Partner: For continuous monitoring and layered protection
Final Thoughts: Every Second Counts
The ToolShell exploit campaign represents one of the most sophisticated and damaging zero-day chains seen against enterprise infrastructure in 2025. Even after patching, stolen cryptographic secrets could allow ongoing compromise — unless addressed proactively.
Conclusion: Defend Your Business Before It’s Too Late
Our team combines deep technical expertise, real-time threat intelligence, and rapid response capabilities to ensure your systems are protected, resilient, and fully restored with minimal disruption. In moments like this, speed and strategy matter — and Threatsys stands ready to defend your digital assets when it counts the most.

Over 75 Servers Breached Worldwide — Is Your Organization Next?





