A new set of Bluetooth vulnerabilities has exposed a critical attack surface in millions of modern vehicles. Dubbed PerfektBlue, this exploit chain affects infotainment systems used by major automobile brands and enables remote code execution with minimal user interaction.
At Threatsys, we view this as a wake-up call not just for OEMs, but for everyone building connected systems.
The Vulnerability Chain
PerfektBlue combines multiple flaws in the Opensynergy Bluetooth stack used across vehicle infotainment systems. While each on its own may seem low-impact, chained together, they allow an attacker to take control of the system wirelessly, often with no user approval or alert.
Attackers within Bluetooth range could:
- Inject malicious code into a car’s infotainment system,
- Access sensitive data like GPS, contacts, or call history,
- Potentially pivot into deeper vehicle networks if segmentation is weak.
This isn’t just a Bluetooth bug. It’s a roadmap for remote automotive compromise.
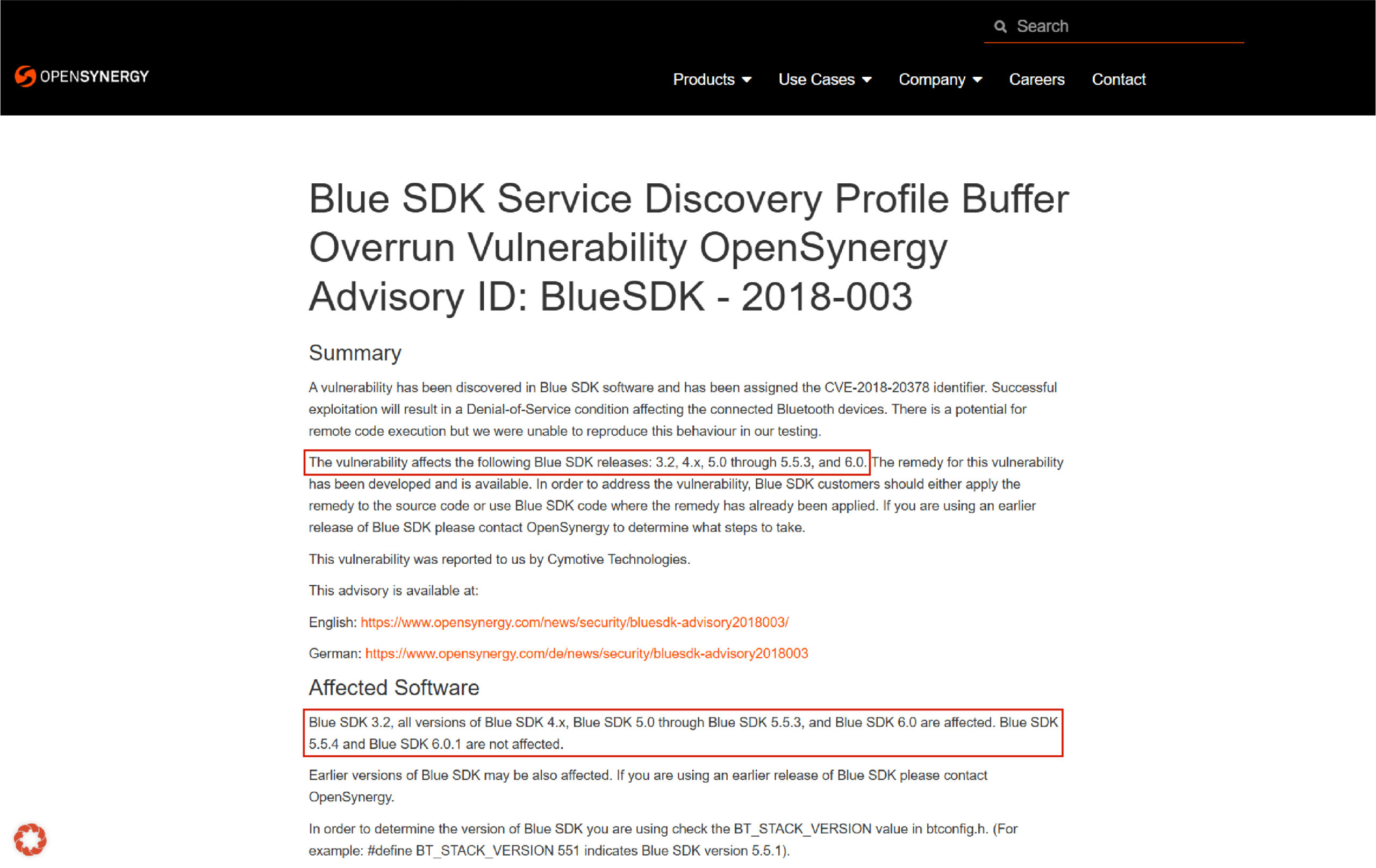
Why This Matters
Most people trust that their car’s infotainment system is “just for music and maps.” But today’s connected vehicles blur the line between convenience and critical infrastructure. When infotainment becomes a gateway to sensitive data or deeper vehicle systems, security gaps can have real-world consequences.
The lack of timely patch rollouts across manufacturers only increases the risk. In our assessment, a Bluetooth-based exploit with RCE potential even if requiring proximity demands immediate attention.
How Threatsys Can Help
At Threatsys, we specialize in securing connected ecosystems from the firmware in your infotainment stack to the broader architecture of your connected vehicles. Here’s how we help OEMs, suppliers, and mobility innovators stay ahead of emerging threats like PerfektBlue:
- Bluetooth Stack Security Audits
We perform in-depth audits of your Bluetooth protocol stack, SDKs, and implementations — identifying vulnerabilities, misconfigurations, and overlooked exploit chains. Our audits cover legacy, custom, and vendor-supplied stacks to ensure nothing slips through the cracks. - Embedded Firmware Hardening & Exploit Simulation
Threatsys simulates real-world attacks on your firmware to identify RCE vectors, memory corruption issues, and privilege escalation paths. We don’t just test — we provide hardened alternatives and secure design patterns that reduce exposure at the code level. - Secure OTA & Update Infrastructure Reviews
Remote updates are powerful — but when unprotected, they’re dangerous. We assess your OTA delivery pipeline, authentication mechanisms, rollback protections, and encryption standards to ensure updates don’t become a weapon in the wrong hands. - Threat Modeling for Connected Vehicle Architectures
Our experts map out your full attack surface — from infotainment to backend — identifying trust boundaries, data flow weaknesses, and lateral movement risks. This gives you a proactive security blueprint tailored to your platform’s architecture. - Red Team Engagements for Automotive Platforms
Want to know how attackers will actually come for your systems? We’ll show you. Threatsys conducts red team simulations tailored for automotive environments — testing your defenses, your incident response, and your assumptions.
Security Starts at the Stack
PerfektBlue is a classic example of how deeply embedded flaws can ripple through the supply chain. The weakness didn’t start with the car, it began in a third-party SDK. Yet it impacts millions of drivers.
Security isn’t just about protecting the end-product. It’s about owning every layer of what goes into it.
Final Thoughts
PerfektBlue won’t be the last Bluetooth-based vulnerability—nor the most dangerous. As systems grow more connected, complexity becomes the enemy of security. What looks like a harmless protocol stack can become an open door.
The only defense? Relentless auditing, rapid patching, and an embedded security-first mindset.
Conclusion: Don’t Let Convenience Become a Compromise
PerfektBlue is more than just a Bluetooth vulnerability — it’s a warning. As vehicles become smarter and more connected, the attack surface is growing faster than most security programs can adapt. What seems like a minor protocol flaw today can turn into a full-scale system compromise tomorrow.
At Threatsys, we believe security must evolve as fast as innovation does. Whether you’re designing next-gen infotainment systems, rolling out OTA infrastructure, or managing a fleet of connected vehicles — now is the time to rethink embedded security.

Let’s secure the future, one stack at a time.





